Overview
Connect your AWS account to Annie to enable real-time infrastructure mapping, monitoring, and intelligent insights. Annie will ingest your AWS resources and relationships to build a comprehensive knowledge graph of your cloud environment.Setup Guide
- Go to the Anyshift integrations page
- Navigate to the AWS section
- Follow the setup instructions to connect your AWS account
Option 1: IAM Assume Role (Recommended)
Option 1: IAM Assume Role (Recommended)
Step 1: Create the IAM Role
Use one of these methods to create a role with read-only permissions:- Using Terraform (Recommended)
- Using AWS Console
- Navigate to IAM Roles and select Create Role.
- Choose Another AWS account and enter the Account ID:
211125758836. - Add an External ID (Optional: Acts as a shared secret).
- Attach the AWS-managed policy ReadOnlyAccess.
- Complete the role creation process.
- Copy the Role ARN for the next step.
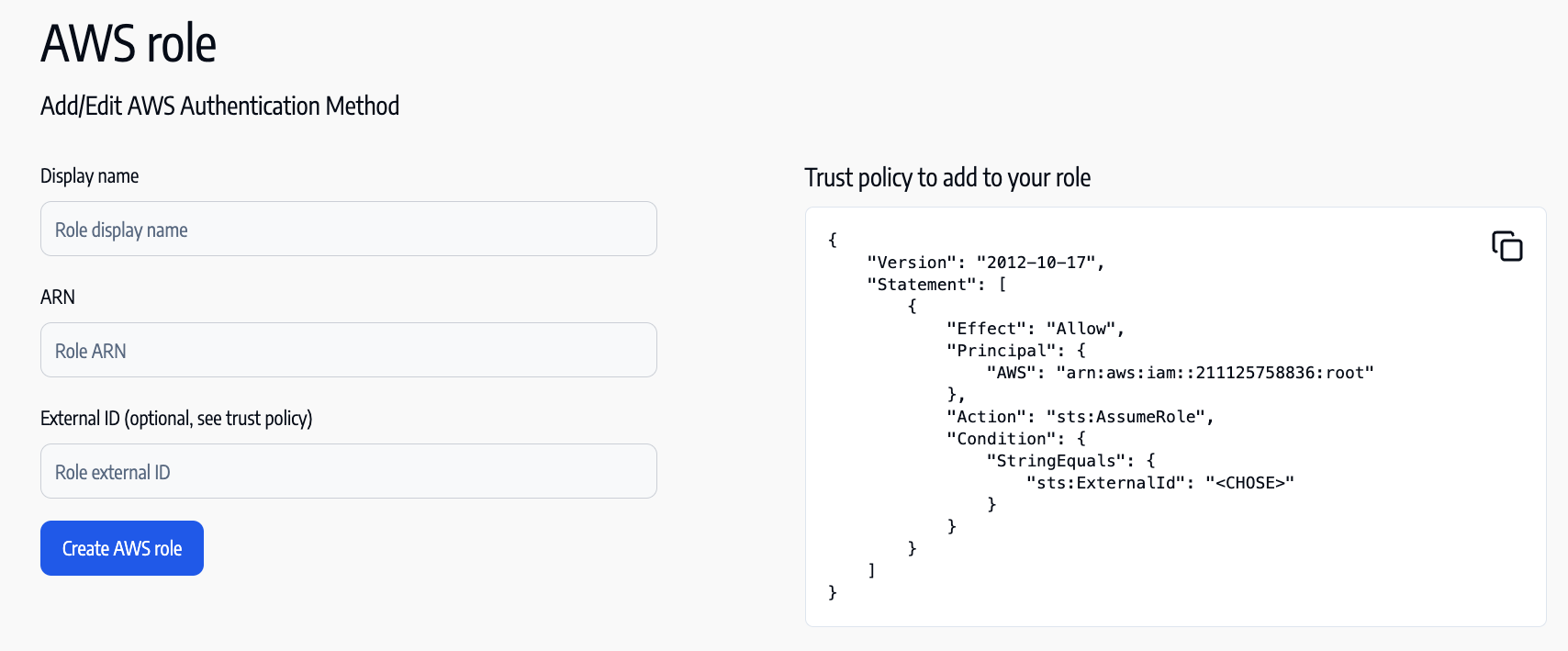
Step 2: Add the IAM Role to Anyshift
- Navigate to Anyshift Configuration and select Add AWS Role.
- Enter a descriptive Display Name for the role (e.g.,
"read_only_role_for_anyshift"). - Paste the Role ARN from the previous step.
- Enter the External ID (Optional)
- Save the configuration.
Option 2: IAM User
Option 2: IAM User
Step 1: Create IAM User
Choose your preferred method:- Using Terraform (Highly Recommended)
- Using AWS Console
- Go to IAM → Users → Add User
- Enable Programmatic Access
- Attach “ReadOnlyAccess” policy
- Save Access Key ID and Secret Access Key
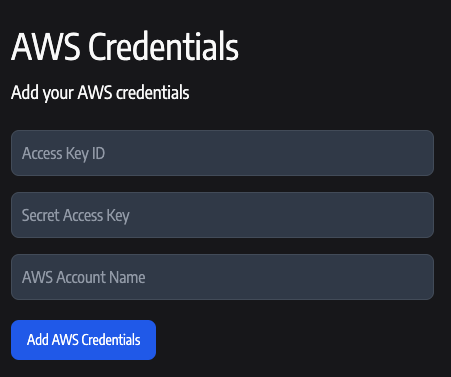
Step 2: Configure in Anyshift
- Enter the Access Key ID and Secret Access Key you obtained from the IAM user creation step.
- Provide a descriptive AWS Account Name label (e.g.,
"read_only_user_for_anyshift").
Custom Permissions (Optional)
Custom Permissions (Optional)
For granular control, you can limit access to specific resources:This provides read-only access to common AWS resources while maintaining security best practices.
Features Enabled
Resource Monitoring
Real-time visibility into your cloud infrastructure
Dependency Mapping
Understand your infrastructure dependencies